xbreach
Think Your Defenses Work? Prove It at Enterprise Scale.
XBreach by Thawd is an enterprise-grade Breach and Attack Simulation platform that continuously validates security controls across the organization using controlled, real-world attack simulations delivering centralized visibility, actionable insights, and evidence-based assurance.
XBreach
See your organization through an attacker’s eyes.
Identify real exposure. Prove your defenses.
Identify real exposure. Prove your defenses.

One Platform. Multiple Attack Vectors. Full Control

Data Exfiltration

Significant Data Exfiltration



Files


Web Application Attacks

SQL Injection


XSS


RCE


SQL Injection


LDAP Injection


Endpoint attacks

Defense Evasion


Privilege Escalation


Persistence


Credential Dumping


Zero-Day Behavior


E-mail Infiltration

Email Enumeration


malicous pdf


Domain spoofing


malicous links


Network Attacks

Beaconing




Active Directory

Reconnaissance


Lateral Movement


Credential Access


Persistence


Privilege Escalation


Exploitation

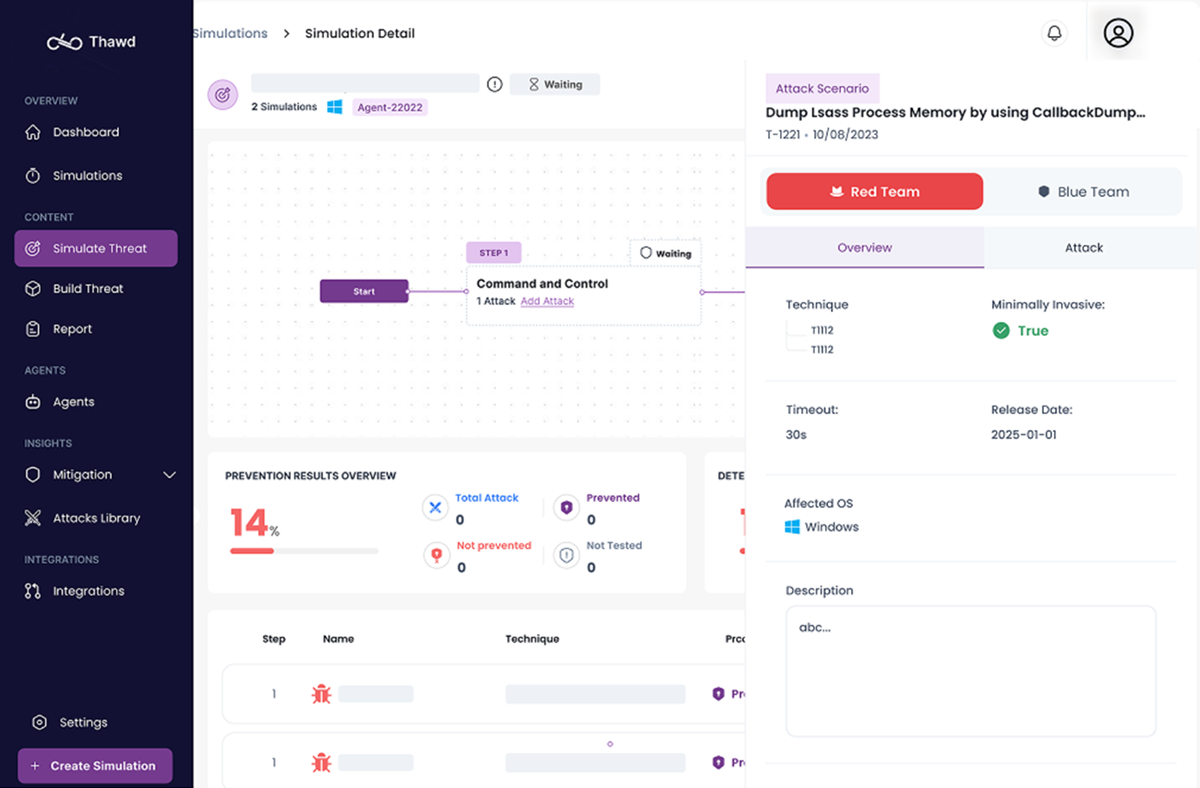
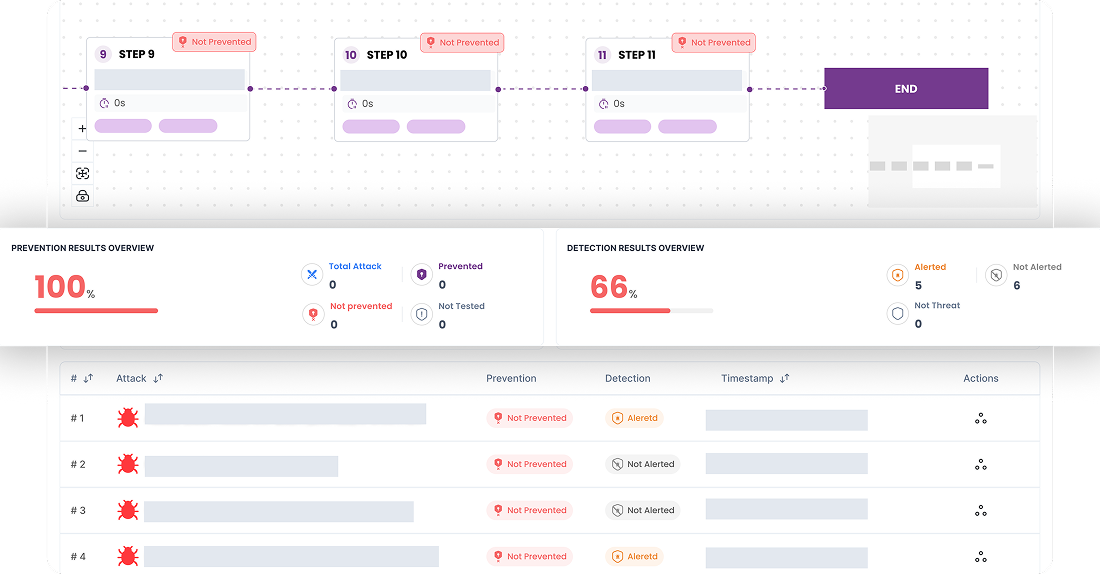
How XBreach Attack Simulation Works?
Step 1
Deploy & Connect Agents
Deploy XBreach agents across multiple endpoints and environments.
All agents securely connect to the central XBreach platform, enabling enterprise-wide orchestration and visibility.
All agents securely connect to the central XBreach platform, enabling enterprise-wide orchestration and visibility.
Step 2
Choose or Customize a Threat
Select a prebuilt threat scenario from the library or create your own custom threat. Review the attack steps and techniques that will be executed during the simulation.
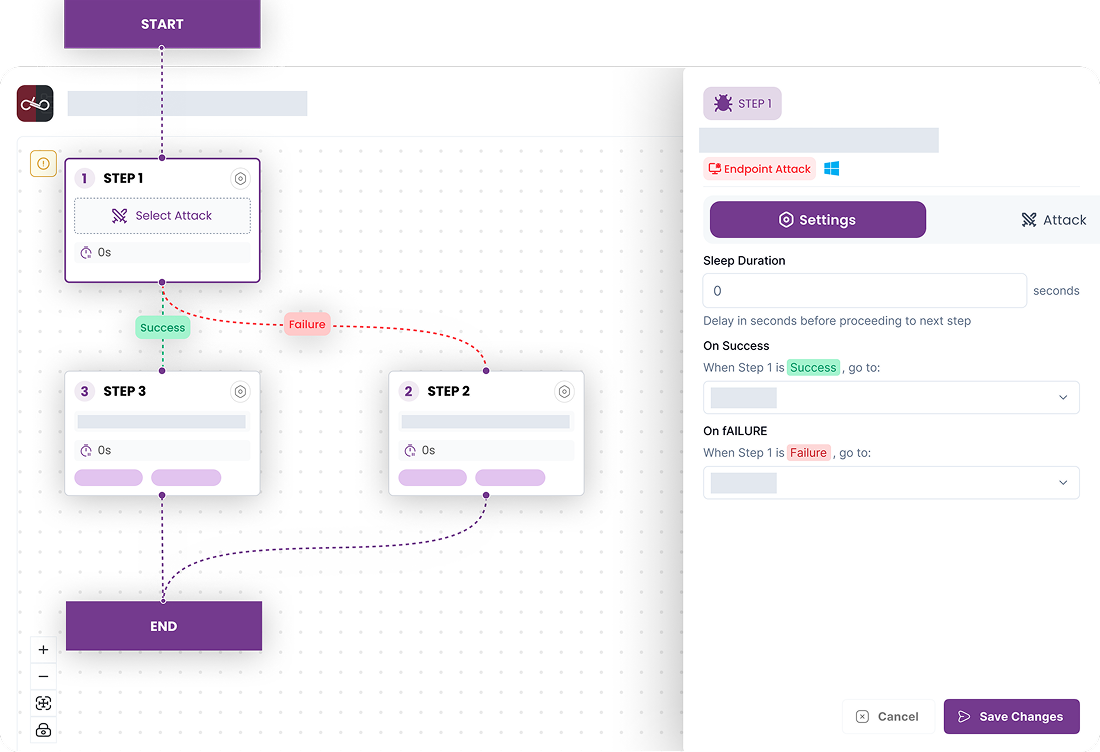
Step 3
Run the Simulation
Launch the simulation and monitor it in real time as each attack step is executed. Watch the simulation unfold live until completion.
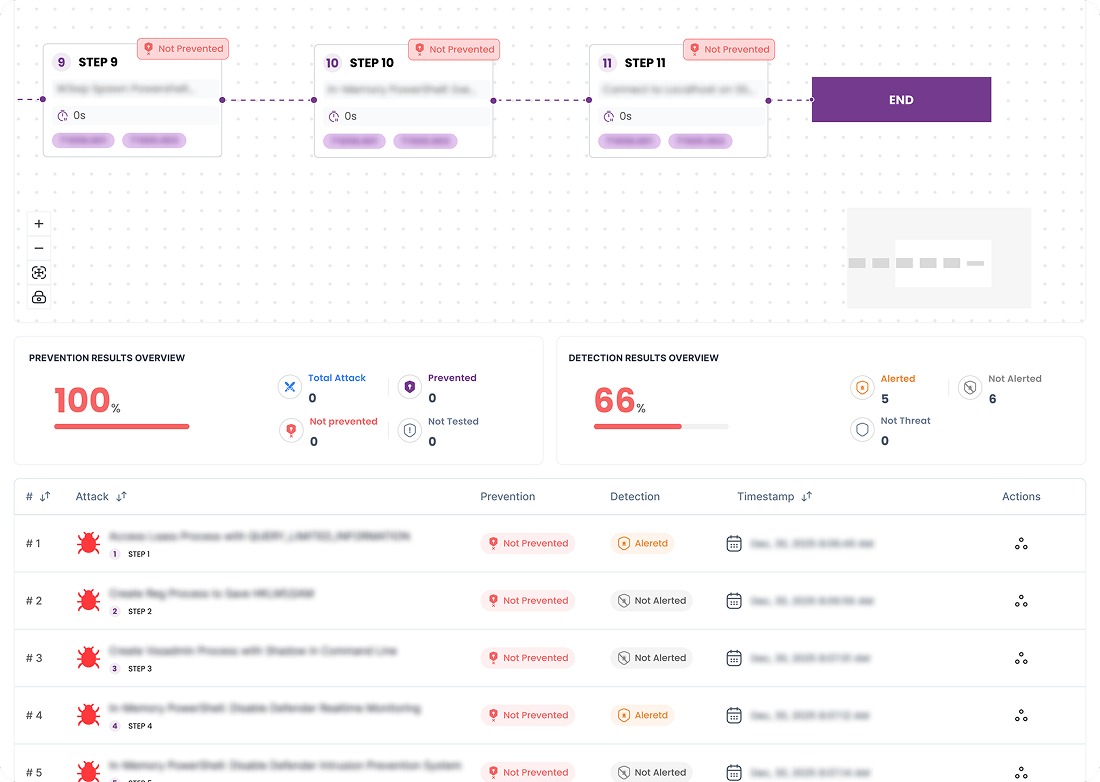
Step 4
Review the Results
Access a centralized, enterprise-wide simulation report covering attack execution across endpoints, detection and prevention outcomes, and validation results. Use these insights to improve detection coverage, response workflows, and overall security posture.

Example of Usage
.svg)
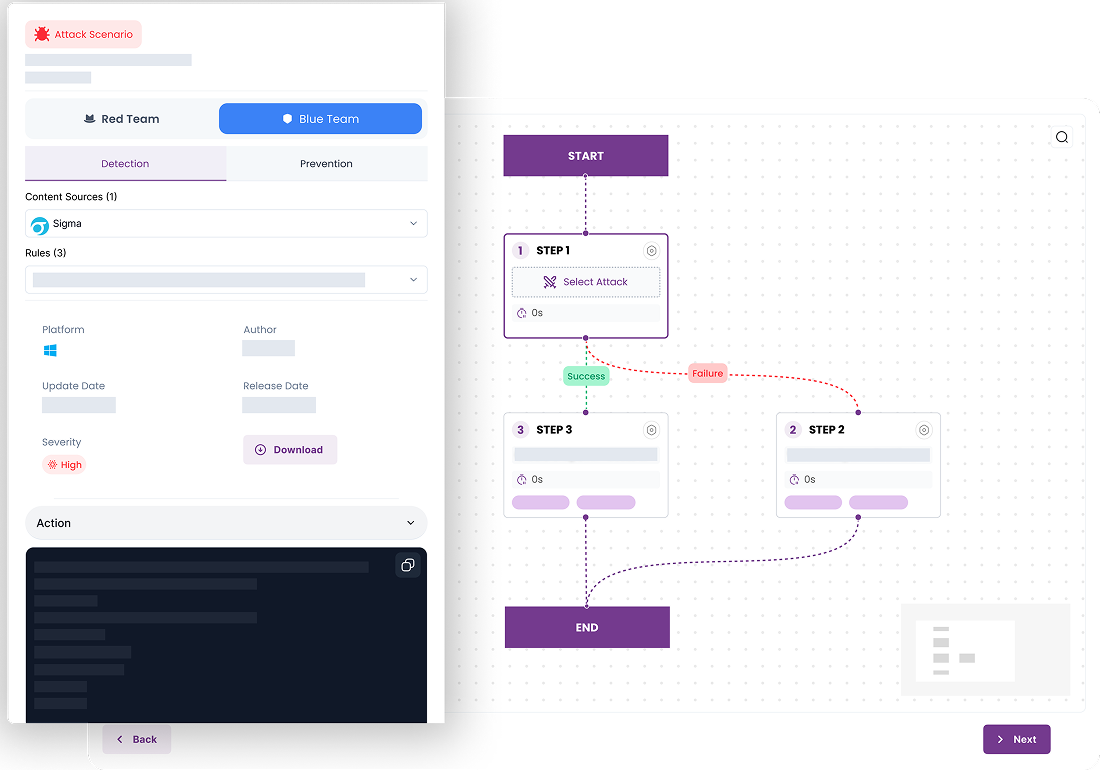
NCA Compliance & Audit Policy Validation
National entity used SimLight to validate Sigma rules and Windows audit policies automatically.
Outcomes:
Identified misconfigurations
Align with NCA standards
Validates detection rules easily
.svg)
SOC Readiness Testing
An enterprise simulated real attacks to test their SOC’s detection and response capabilities.
Outcomes:
Identify and fix critical detection gaps.
Improve SOC readiness against threats.
Maximize value from security controls.
.svg)
EDR & SIEM Validation in an Organization
SimLight continuously tested EDR and SIEM tools using realistic attack behaviors.
Outcomes:
Identified hidden blind spots
Proved security control effectiveness
Validated threat detection coverage across MITRE ATT&CK
integrations
Make Your Security Stack Prove It Works
XBreach integrates with your existing security stack including EDR, SIEM, and core security controls to continuously validate detections, response logic, and control effectiveness using real-world attack simulations Rather than replacing your tools, XBreach tests them in production-safe conditions, giving teams clear evidence of what works, what fails, and what has drifted over time.
With XBreach integrations, your teams can:
Validate EDR and SIEM detections in real conditions
Test correlation rules, alerts, and response workflows against realistic attacker behavior mapped to MITRE ATT&CK.
Test correlation rules, alerts, and response workflows against realistic attacker behavior mapped to MITRE ATT&CK.
Detect control drift and silent failuresIdentify when detections stop firing due to configuration changes, updates, or environmental drift.
Improve security posture without disruptionRun controlled attack simulations safely, without impacting production systems or business operations.

Compliance Achieved



See XBreach In Action
Submit a request and we'll share answers to your top security validation and exposure management questions.
Contact Us


















