Elevate Your Defense Challenge Your Security With Thawd
At Thawd, we specialize in enabling organizations to continuously validate their security controls As pioneers in Breach and Attack Simulation (BAS), our technology offers 24/7 actionable insights for enhancing threat prevention and detection.
Trusted By





















Validate Your Security Controls Before Attackers Do
uncover hidden weaknesses in your defenses — before they’re exploited. Simulate real-world threats, validate your controls, and empower your team to respond faster and smarter.

Instantly Know Where You’re Exposed

Prioritize What Matters

Strengthen Defenses Faster
Continuous Security Validation
Thawd continuously simulates real-world cyber threats to test how well your defenses detect, respond, and recover — ensuring non-stop validation of your security posture.
Actionable Recommendations
Thawd delivers detailed, step-by-step guidance to help your team quickly mitigate risks — all aligned with MITRE ATT&CK and NCA compliance frameworks.
Continuous Security Validation
Thawd continuously simulates real-world cyber threats to test how well your defenses detect, respond, and recover — ensuring non-stop validation of your security posture.
Enhanced Cyber Resilience
Thawd empowers your organization to build stronger defenses, respond faster, and stay resilient against emerging cyber threats.
Identification of Security Gaps
By emulating advanced attack techniques, Thawd reveals weaknesses in both prevention and detection layers, helping you prioritize improvements.




Products
Explore Our Products
SimLight
Lightweight Agent to Validate NCA Sigma Rules and more
Single Lightweight Agent
A single lightweight agent that can be installed on any system without affecting its resources.
A single lightweight agent that can be installed on any system without affecting its resources.
Highest Quality Threat Intelligence
The agent utilizes threat intelligence provided by the NCA, which is the best available CTI for Saudi entities.
The agent utilizes threat intelligence provided by the NCA, which is the best available CTI for Saudi entities.
Minimally Invasive Attacks
Engineered to execute only the necessary actions to validate detection rules efficiently, ensuring comprehensive coverage without impacting the environment.
Engineered to execute only the necessary actions to validate detection rules efficiently, ensuring comprehensive coverage without impacting the environment.
Learn More


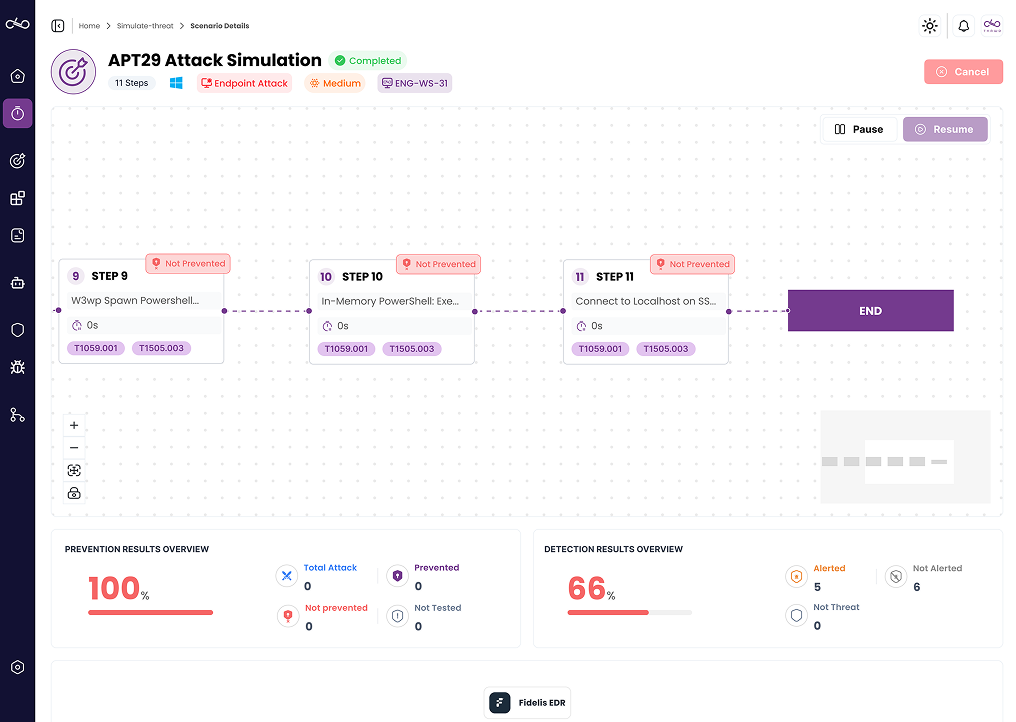
XBreach
Advanced Platform for Continuous Security Testing & Threat Simulation!
Security Control Integration
Integrate with SIEM and EDR for seamless continuous validation
Integrate with SIEM and EDR for seamless continuous validation
Scheduled Simulations
Scheduled Simulations to protect against operational drifts and silent failures
Scheduled Simulations to protect against operational drifts and silent failures
Custom Attacks and Scenarios
Implement custom attacks based on proprietary threat intelligence with ease
Implement custom attacks based on proprietary threat intelligence with ease
Learn More

Efficiently manage complex ecosystems.
Thawd continuously simulates real-world cyber threats to test how well your defenses detect, respond, and recover — ensuring non-stop validation of your security posture.
Thawd by the Numbers
Proven impact. National expertise. Real-world simulations.
50+
Organizations tested their defenses using Thawd.

98%
Customer satisfaction across government and enterprise deployments.

100%
Average improvement in detection and response capabilities within 60 days.

3000+
Real-world threats simulated with high accuracy using local threat intelligence.


awards
Awarded By The Industry

WINNER
Cyber Security Challenge
SITE & Monshaat
SITE & Monshaat

WINNER
CYBRIC Innovation
NCA & NEOM
NCA & NEOM


See Thawd In Action
Submit a request and we'll share answers to your top security validation and exposure management questions.
Contact Us













